Scope
The purpose of this policy is to give clear understanding of what The YubiKey is and inform on the usage within the company.
1. What is a YubiKey
The YubiKey is a hardware authentication device manufactured by Yubico to protect access to computers, networks, and online services that supports one-time passwords (OTP), public-key cryptography, authentication, the Universal 2nd Factor (U2F) and FIDO2 protocols developed by the FIDO Alliance.
It allows users to securely log into their accounts by emitting one-time passwords or using a FIDO-based public/private key pair generated by the device.
YubiKey also allows for storing static passwords for use at sites that do not support one-time passwords. Google, Amazon, Microsoft, Twitter, and Facebook use YubiKey devices to secure employee accounts as well as end user accounts.
2. Setup and Use
2.1 Setup
Setting up your YubiKey isn't that different from setting up app-based two-factor authentication. The set-up varies from platform to platform. In general, just go to the platform settings
=> Select 2fa and proceed with setting the security key. Once this is done, you will have to follow all the information on the platform in order to associate your YubiKey with your account.
If you need assistance in setting up your YubiKey, you can ask the technical helpdesk or take a look at the user manual provided by the end customer.
2.2 Use
Using YubiKey is extremely simple, just enter it when you are written and then follow the instructions on the screen. As a rule, YubiKey is asked of you only in particular conditions, such as for access or during specific operations that requires authorization. The rest of the time, the YubiKey must be disconnected from the computer.
As said before how this works is going to vary from app to app, but I'll use Google as an example. Follow the instruction for Google, and you'll find a link with instructions for adding your YubiKey to your Google account, which offers a link for adding your key.
A useful link on how to use YubiKey is the manufacturing site yubico.com
3. Lifecycle Management
- Fiber Group keeps track of who has which YubiKey credentials and provides visibility by enquiry, reports and API
- As Fiber Group tracks who has which YubiKey credentials, it provides the company the ability to revoke and replace credentials as employment status or rights change
- Lifecycle operations are audited, providing visibility and reporting over management operations in addition to authentication operations
- UsingFiber Group security policies, the Fiber Group authentication service will determine how a user is allowed to authenticate and walk the user through the authentication process
- Once authenticated, Fiber Group authentication service will then communicate via the plug-in with ADFS to grant access to the end system
4. Issuance
- All YubiKey are the property of Fiber Group, they are temporarily entrusted to the user for use as an authentication factor. But they remain the property of Fiber Group Shpk.
- The users in the company, who have a yubikey assigned, must take care of it, never sharing it with anyone and avoiding damaging it in any way.
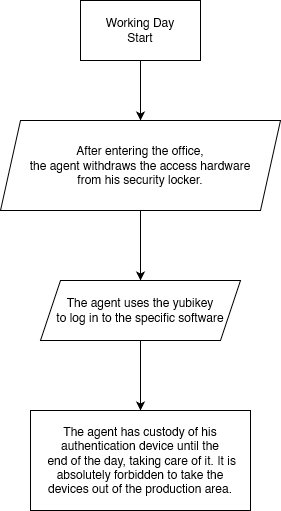
- All users must deposit the YubiKey, at the end of the work or in any case when it is not used for authentication purposes according to the provisions of the Line Manger / Team Leader.
- The YubiKey can never leave the Fiber Group Shpk headquarters located in Tirana, or when specified the protection area associated with it.
- All YubiKey must be picked up at the start of their shift and stowed away at the end of it.
- Issuance policy defines how a user must authenticate before collecting their YubiKey credentials, options include OTP
- Use of a YubiKey by a person other than to whom it is assigned is forbidden.
- Upon assignment and during use, employees are responsible for reporting any damage to Fiber Group. Employees will assume the cost of any unreported damages. The YubiKey agreement is revisited every time an employee damage the YubiKey.
5. YubiKey store and Check-in Check-Out procedure
As established in the policy, the Yubikey can never leave the production area and in some cases the fiber 5 headquarters. The procedure for storing the hardware is described below.
All Yubikeys must be labeled with a unique ID corresponding to the operator's use. The list of Key ID and Operator User matches must be kept safe, in a safety deposit box and not directly with the keys.
The Yubikeys are stored in special transparent cabinets assigned to each operator inside the production area. These inspectable lockers are able to let the Manager know if all the Yubikeys have been stowed away at the end of the day.
At the start of each shift, the secretary initiates the key distribution process. They retrieve the keys from the secure box and hand them out to the respective employees who are scheduled for that shift.
To ensure a proper record, the employees sign a report indicating that they have received the keys. The secretary then securely returns any remaining keys to the box until the next shift begins.
Once the secretary identifies a set of keys that have not been collected, they take the initiative to send an email notifying the Workforce Management team about this issue. In the email, they have also included the Floor manager and the HR department by adding them as recipients in the email's copy.
After receiving the email from Workforce Management (WFM) regarding resource shifts and absences, the secretary cross-checks the information provided with the number of keys stored in the closet and the signatures recorded in the report. This ensures that there is alignment between the key distribution and the WFM's communication.
At the end of each shift, the secretariat consistently performs a thorough check of the keys, collected signatures, and the presence of Yubikeys in the Production Area. If any anomalies or discrepancies are discovered, the secretariat promptly sends an email to the operation, while also copying the HR and Legal, Compliance & Audit departments.
To ensure adherence to proper procedures, the Legal Compliance & Audit team conducts weekly inspections to verify whether the established protocol is being followed accurately.
Check-in Operations:
The check-in procedure is carried out through the following phases:
It is understood, as previously written, that MFA hardware devices must never leave the production area. The same must be put away in the security locker at each exit from the area as per procedure and taken back at the time of return.